
Guide to Social Engineering Attacks
Today, most businesses are aware of cyberattacks and have invested many resources in preventative measures. However, there is one variable to consider in this digital world — humans. Cyber attackers take advantage of this variable to bypass a business’s security measures. They call this social engineering.
According to IBM’s 2023 Cost of a Data Breach Report, social engineering tactics can have significant financial consequences. The report states that the average cost of data breaches caused by social engineering tactics exceeded $4.5 million. This startling statistic highlights the consequential risk these manipulative tactics pose to businesses.
But by arming yourself with knowledge, you can safeguard your company. Our guide to social engineering attacks will help you to recognize, stop and prevent these threats. Let’s start fortifying your company’s defenses.
What Are Social Engineering Attacks?
Social engineering attacks are manipulative tactics used by cybercriminals to trick individuals. So, instead of exploiting technical vulnerabilities, attackers prey on human psychology and behavior. They leverage trust, fear, curiosity or urgency. But why do cyber attackers commonly use social engineering attacks?
The answer lies in their effectiveness. It’s often easier to deceive a person than to hack through sophisticated security systems. Verizon’s 2024 Data Breach Investigations Report highlights this. It states that 68% of security breaches included a non-malicious human factor. Cybercriminals know they can breach even the most secure networks with enough convincing.
The primary objectives of these attacks include the following:
- Steal sensitive information, such as login credentials, financial data or intellectual property (IP).
- Gain unauthorized access to systems for further exploitation, such as installing malware or launching broader cyberattacks.
However, businesses can better prepare and protect themselves by understanding social engineering attacks.
Types of Social Engineering Attacks
Social engineering attacks come in various forms. Identifying social engineering attempts is simpler once you’re aware of the basic modus operandi. Here are some of the most common types:
Phishing

Phishing is the most prevalent social engineering attack method. According to IBM’s report, it’s also the most expensive, exceeding $4.7 million in costs. Phishing attacks consist of an email or text message pretending to be from a reliable source requesting information. These emails often contain links to fake websites designed to capture your data.
For example, a person may receive an email from their “bank” asking them to “verify” their security details. The “verification link” leads them to a fraudulent website that captures their login information.
Types of phishing include:
- Spear phishing: Businesses, in particular, must be vigilant for spear phishing. This version targets an individual in a company by sending them an email pretending to be from a senior executive. The cyber attacker requests sensitive information through this email.
- Vishing: Vishing is short for voice phishing and involves phone calls. With vishing, attackers pretend to be a co-worker or a legitimate organization. For example, they may claim to be a member of the IT helpdesk, soliciting login details.
- Smishing: Smishing is short for SMS phishing and involves text messages. Instead of using vishing, attackers may send messages to achieve their goals. Smishing messages can contain malicious links or prompt you to provide personal information under pretenses.
Baiting
As the name suggests, baiting involves leaving bait or creating a trap for unsuspecting victims. Attackers may leave a physical device, such as a USB stick, in a conspicuous location. When someone picks it up and plugs it into their computer, the USB stick installs malware, giving the attacker access to the system.
Pretexting
Attackers create a fabricated scenario or pretext to gain information. They might pose as someone needing help, like an IT support technician, to trick you into revealing passwords or other sensitive data.
Quid Pro Quo
This attack promises a benefit in exchange for information. For example, an attacker might offer a free software update or tech support in return for access to your computer or network.
Tailgating
Tailgating, or “piggybacking,” involves a physical security breach. It can happen when an unauthorized person follows an authorized individual into a restricted area. It can be as simple as an attacker following an employee into a building by discreetly slipping through an unlocked door.
However, tailgating can also be a digital security breach. For example, an individual walks away from their computer without logging out of a personal account or network.
Real-Life Social Engineering Attack Examples
Here are a few real-life examples to help you better understand the effect of social engineering.
Rimasauskas $100 Million Spear Phishing Scam
Evaldas Rimasauskas and his team set up a fake company to impersonate a computer manufacturer. The big thing about this impersonation is that this manufacturer worked with Google and Facebook. They sent phishing emails to specific employees and directed them to deposit money into fraudulent accounts. As a result, they cheated the tech giants out of over $100 million over two years.
The Microsoft 365 Phishing Ploy
Disguised as a price revision notification, this Business Email Compromise (BEC) scam duped many. It tricked recipients into installing malicious code disguised as an Excel spreadsheet file. Upon opening the file, targets are directed to a website containing malicious code that prompts them to re-enter their Microsoft 365 login credentials. As a result, the inserted credentials were then sent to cybercriminals.
Sacramento County’s Phishing Nightmare
Employees at Sacramento County fell victim to a phishing attack. This attack exposed over 2,000 records of health information and over 800 records of personal information. Attackers sent phishing emails containing a link to a malicious website where targets entered their usernames and passwords.
How Fraudsters Mimicked Government Authority
In 2022, a sophisticated phishing attack imitated the US Department of Labor’s email domain and branding. The email invited recipients to bid on a government project. The phishing emails were well written and included a fake bidding instruction document with a “Bid Now” button. This led targets to enter their Office 365 credentials on a phishing site.
OCBC’s Battle Against Phishing Attacks
A string of phishing attacks targeted overseas Chinese Banking Corporation (OCBC) customers. This phishing attack led to approximately $8.5 million in losses. The emails duped customers into giving up their account details. Even after the bank shut down fraudulent domains, the attackers quickly set up new accounts to continue their fraudulent activities.
How to Recognize Social Engineering Attacks
Stay vigilant by recognizing the telling signs of social engineering attacks beforehand. Here are critical indicators to watch for:
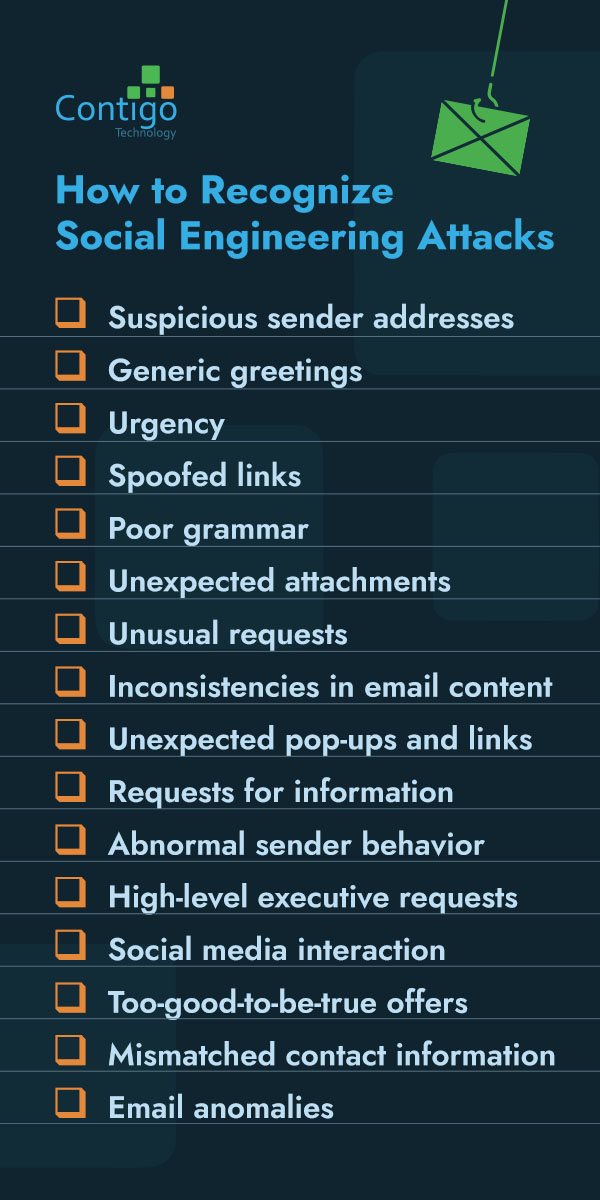
- Suspicious sender addresses: Always scrutinize the sender’s email address. Attackers often use addresses that look legitimate but may have slight misspellings or unusual domain names.
- Generic greetings: Be wary of emails that start with generic greetings like “Dear Customer” instead of using your name.
- Urgency: Attackers often create a sense of urgency. Their messages usually claim that you must take immediate action to avoid serious consequences. This pressure is designed to prevent you from thinking critically.
- Spoofed links: Hover over links without clicking to check the actual URL. Spoofed links may appear legitimate initially but direct you to a malicious site.
- Poor grammar: Poor grammar and spelling errors are common in phishing emails. This is because they often originate from non-native speakers or automated tools.
- Unexpected attachments: Be cautious of unexpected email attachments, especially from unknown senders. These attachments can contain malware designed to compromise your system. Even if the sender appears familiar, verify the legitimacy of the attachment before opening it.
- Unusual requests: Be cautious if an email or message requests sensitive information. Be vigilant if they ask for any passwords, credit card numbers or personal identification details. Legitimate organizations typically do not ask for such information via email.
- Inconsistencies in email content: Look for inconsistencies in the message. These inconsistencies can include mismatched email addresses, logos or other branding elements. Email content from legitimate sources must align with the official organization’s style.
- Unexpected pop-ups and links: Be wary of unexpected pop-ups or links asking for credentials or personal information. This is especially true if they appear while you’re on a legitimate website.
- Requests for information: Messages requesting confidential company information or proprietary data should be treated with suspicion. This is particularly true if they come from unknown sources or seem out of the ordinary.
- Abnormal sender behavior: Pay attention to unusual behavior from known contacts. These behaviors could include out-of-character language or requests that seem odd or urgent. This abnormality may indicate their email account is compromised.
- High-level executive requests: Be suspicious of emails from high-level executives asking for financial transactions or sensitive information. This is especially the case if they create a sense of urgency or bypass regular protocols. Verify such requests through a different communication channel.
- Social media interaction: Be cautious of interactions through social media platforms that request personal information or direct you to unknown websites. Attackers often use social media to gather information and launch phishing attacks.
- Too-good-to-be-true offers: Offers that seem too good to be true, usually are. An example could be winning a lottery you never entered or receiving a large sum of money from an unknown source. These are often scams designed to steal your information.
- Mismatched contact information: Verify the contact information provided in the email with known contact details of the organization. Discrepancies in phone numbers, email addresses, or physical addresses can be a sign of a scam.
- Email anomalies: Check for anomalies in emails or messages. Look for indicators like unusual time stamps, sender locations that don’t match the sender’s known location or email headers that look suspicious when inspected.
How to Prevent Social Engineering Attacks
It’s better to know how to stop social engineering attacks before they happen. This proactive approach requires collaboration between employers and employees. Here are 18 strategies to help prevent social engineering attacks:
1. Access Control
Install strict access control measures to ensure that employees only have access to the information necessary for their roles. Limit administrative privileges to reduce the risk of unauthorized access.
2. Behavioral Analytics
Use behavioral analytics tools to establish a baseline of normal user behavior. These tools can detect anomalies that may indicate a compromised account or a social engineering attack in progress.
3. Continuous Monitoring
Implement continuous monitoring of your systems to detect unusual activities. It can help identify potential threats early and take swift action to mitigate risks.
4. Data Encryption
Encrypt sensitive data at rest and in transit. Encryption adds an extra layer of security, making it more challenging for attackers to access and exploit stolen information.
5. Digital Footprint Management
Manage your digital footprint by limiting the amount of sensitive information shared online. Encourage employees to adjust their privacy settings on social media and avoid oversharing information that attackers could use.
6. Educate Employees
Train employees on the latest social engineering tactics. Conduct phishing simulations and workshops to reinforce their awareness and improve their ability to identify and avoid these attacks. An informed team is your first line of defense.
7. Incident Response Plan
Develop and maintain an incident response plan. These plans must outline the steps to take when a social engineering attack is suspected or detected. Ensure all employees are familiar with this plan and conduct regular drills to test its effectiveness.
8. Install MFA
Multi-factor authentication (MFA) adds an extra layer of security. Users must provide two or more verification factors to access systems or accounts. MFA makes it harder for attackers to gain unauthorized access, even if they steal a password.
9. Next-Gen Cloud-Based WAF
Use a next-generation web application firewall (WAF) that provides advanced protection. These firewalls can help detect and block malicious traffic. As a result, it can ensure your applications and data remain secure.
10. Penetration Testing
Conduct penetration testing to identify and address system vulnerabilities. It simulates real-world attacks and helps you understand potential weaknesses that cybercriminals could exploit.
11. Physical Security
Enhance physical security measures to protect against social engineering attacks that involve physical access. Use security badges, surveillance cameras and access control systems to monitor and restrict physical access to sensitive areas.
12. Regular Security Updates

Keep your software, systems and applications updated with the latest security patches. Regular updates fix known vulnerabilities, reducing the risk of exploitation by attackers.
13. Report Suspicious Activity
Encourage employees to report any suspicious activity immediately. Quick reporting can help your security team respond and mitigate potential threats.
14. Secure Communication Channels
Use secure communication channels for sensitive information. Encourage the use of encrypted messaging apps and secure email services for internal and external communications.
15. Spam Filters
Install spam filters. They can help reduce the number of phishing emails and other malicious messages reaching your employees. Spam filtering may lower the chances of a successful social engineering attack.
16. Vendor and Third-Party Security
Ensure that vendors and third-party partners adhere to your security standards. Conduct regular security assessments and audits to identify and address any vulnerabilities within their systems.
17. Verify Requests
Always verify the legitimacy of requests for sensitive information. If an email or phone call asks for confidential data, contact the requester using known contact information. Otherwise, contact your IT department for assistance. This simple step can prevent many attacks.
18. Zero Trust Architecture
Adopt a zero-trust security model, which operates on the principle of “never trust, always verify.” This approach ensures that all access requests are vetted, regardless of their origin within or outside the network.
If managing these strategies feels overwhelming, consider partnering with a specialized IT security company. Experts can provide tailored solutions and continuous support. They can help your business stay protected against evolving social engineering threats.
Partner With Contigo Technology for Your Cybersecurity Needs

Always opt for a proactive approach. Businesses can protect their operations from threats by staying informed and vigilant. Implementing various preventative measures adds that extra layer of security.
However, managing cybersecurity can be challenging, especially with the day-to-day business demands. This is when an IT services company like Contigo Technology comes into play.
We’re dedicated to providing personalized cybersecurity solutions tailored to your specific needs. Our proactive approach and advanced threat detection capabilities keep us one step ahead of emerging risks. This approach ensures that your sensitive data and systems remain protected.
Contact us online today and trust Contigo to keep your business secure.
